Articles
Technology management insights and technical deep-dives
Google Data Integration: Could It Drive PIDM Adoption?
January 26, 2012 at 12:00 AMInteresting article from Forbes on Google’s privacy announcement and how it will drive the Personal Identity Management industry.
Personal Identity Management (PIDM), is heating up because of three factors:
- The formation of large online networks that collect data about consumers (Google, Facebook, Zynga)
- Web 2.0 technologies and trends to be open platforms creating access to that data
- Increased consumer and government awareness of privacy issues

Picture a Personal Identity Management solution as a dashboard that shows you what these big networks know about you and enable you to update or edit it where the policies allow it.
Permanent Link — Posted in Social Media , Technology Management , EntrepreneurialHuman Nature and Managing Technology Teams
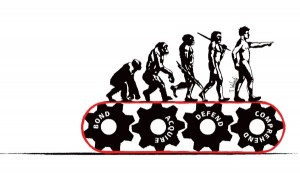
September 9, 2011 at 12:00 AMManaging technology groups can be especially challenging. I attribute this to the way that technology attracts personality types that aren’t as common in traditional business roles. Specifically I am talking about the type of people that founded and continue to support the stereotypes of the technologist - the introverted, over-calm, over-ego’ed nerds and geeks.
Darwin’s Theory of Human Behavior suggests that we are all motivated by four drives: to acquire, to defend what we have acquired, to understand/comprehend the world around us, and to bond socially.
Permanent Link — Posted in Technology ManagementCloud Architecture Best Practices
August 31, 2011 at 12:00 AM“Plan for failure” is not a new mantra when it comes to information technology. Evaluating the worst case scenario is part of defining system requirements in many organizations. The mistake that many are making when they start to implement cloud is that they don’t re-evaluate their existing architecture and the economics around redundancy.
All organizations make trade-offs between cost and risk. Having truly fully redundant architecture at all levels of the system is usually seen as unduly expensive. Big areas of exposure like databases and connectivity get addressed but some risk is usually accepted.
Permanent Link — Posted in Cloud ComputingDisable Akonadi in KDE 4.7
August 22, 2011 at 12:00 AMIn recent KDE updates, the PIM suite (kmail, kontact) is …uh… not really working for me. I don’t know if it is truly broken or just requires a different approach and understanding.
This has me temporarily using Thunderbird for mail until I can get back to using my beloved kmail. Unfortunately, Akonadi, the engine behind the PIM suite, still insists on going out and fetching mail and doing other things.
Permanent Link — Posted in Arch LinuxUnderstanding Cloud Computing Vulnerabilities
August 19, 2011 at 12:00 AMDiscussions about cloud computing security often fail to distinguish general issues from cloud-specific issues.
Here is a great overview from Security & Privacy IEEE magazine of common IT vulnerabilities and how they are impacted by the new cloud paradigm.
The article starts off defining vulnerability in general and then goes on to establish the vulnerabilities that are inherent in cloud computing models.
It really boils down to access:
Of all these IAAA vulnerabilities, in the experience of cloud service providers, currently, authentication issues are the primary vulnerability that puts user data in cloud services at risk
Permanent Link — Posted in Cloud Computing , Security
How The Cloud Changes Disaster Recovery
July 26, 2011 at 12:00 AMData Center Knowledge has posted a great article illuminating the effect that cloud computing is having on the economics of disaster recovery (DR) for information technology. Having fast DR used to mean adding a large considerable expense to your IT budget in order to “duplicate” what you have.
Using cloud technologies not only is this less expensive, but is a great first step towards transitioning IT infrastructure into the cloud paradigm.
Permanent Link — Posted in Cloud ComputingCreative Kryptonite and the Death of Productivity
July 15, 2011 at 12:00 AM“There is often a huge chasm between being busy and being productive.” - great article on the psychology of the modern approach to work
Creative Kryptonite and the Death of Productivity
Permanent Link — Posted in Geek TacticsCloud Computing to Alter Workforce
July 10, 2011 at 12:00 AMThe Charlotte Observer published an article on how cloud computing is changing the roles around in IT. Just knowing hardware and desktop support won’t be enough!
Cloud computing to alter workforce
Permanent Link — Posted in Cloud ComputingBlog Reboot
July 4, 2011 at 12:00 AMI have rebooted the blog. If you are looking for old stuff send me a specific request.
Permanent Link — Posted in Uncategorized